Balancing risk and reward when it comes to security
Cyber security can be expensive and getting budget can be tough. It can be a hard sell for some leaders as the best cyber security is transparent which makes it intangible.
With the budget you do have, it is essential you get the most out of it and your staff are focussed on the risk areas which pose the biggest threat to your business. This is where great risk management comes into play.
Risk management in many organisations can be a tick box exercise for compliance or accreditation purposes such as ISO27001. It brings to mind giant spreadsheets which seem endless combined with hours of meetings to go through each risk line by line. But if you get it right, it allows you to not only make the most efficient and effective budget decisions but can help your team advise leaders at any time, the risk position of the business and the impact any business deliveries or changes will make.
The risk management cycle has four key stages:
- Identify – identify a potential risk or weakness that needs analysed further.
- Analyse – analyse the risk to decide the risk score and next steps.
- Action – take forward the next steps, which can fall into treat, tolerate, transfer or terminate.
- Measure – evaluate whether the action has reduced the risk score or if further weaknesses have been identified.
Kick off with threat modelling workshops
Threat modelling helps you identify and map out the assets an attacker could exploit, the methods they may use, their motivation and what security controls you have in place to mitigate them. This is a useful exercise to do regularly as new threats emerge or your business IT environment changes. Ensure you have the right audience including security, architecture and networks and ask these questions:
- What are my most valuable assets?
- Who would likely target these?
- What routes through our network would allow them to access to these assets?
- How does my supply chain impact this?
During this workshop have a hard look at your security tooling. Are there tools you have bought which are not mentioned as mitigating controls?
Once you understand the threats that exist to your business, you can overlay your current security controls. What is already in place that could mitigate these attacks? You will soon start to see the gaps and vulnerabilities within your environment.
Analyse the gaps
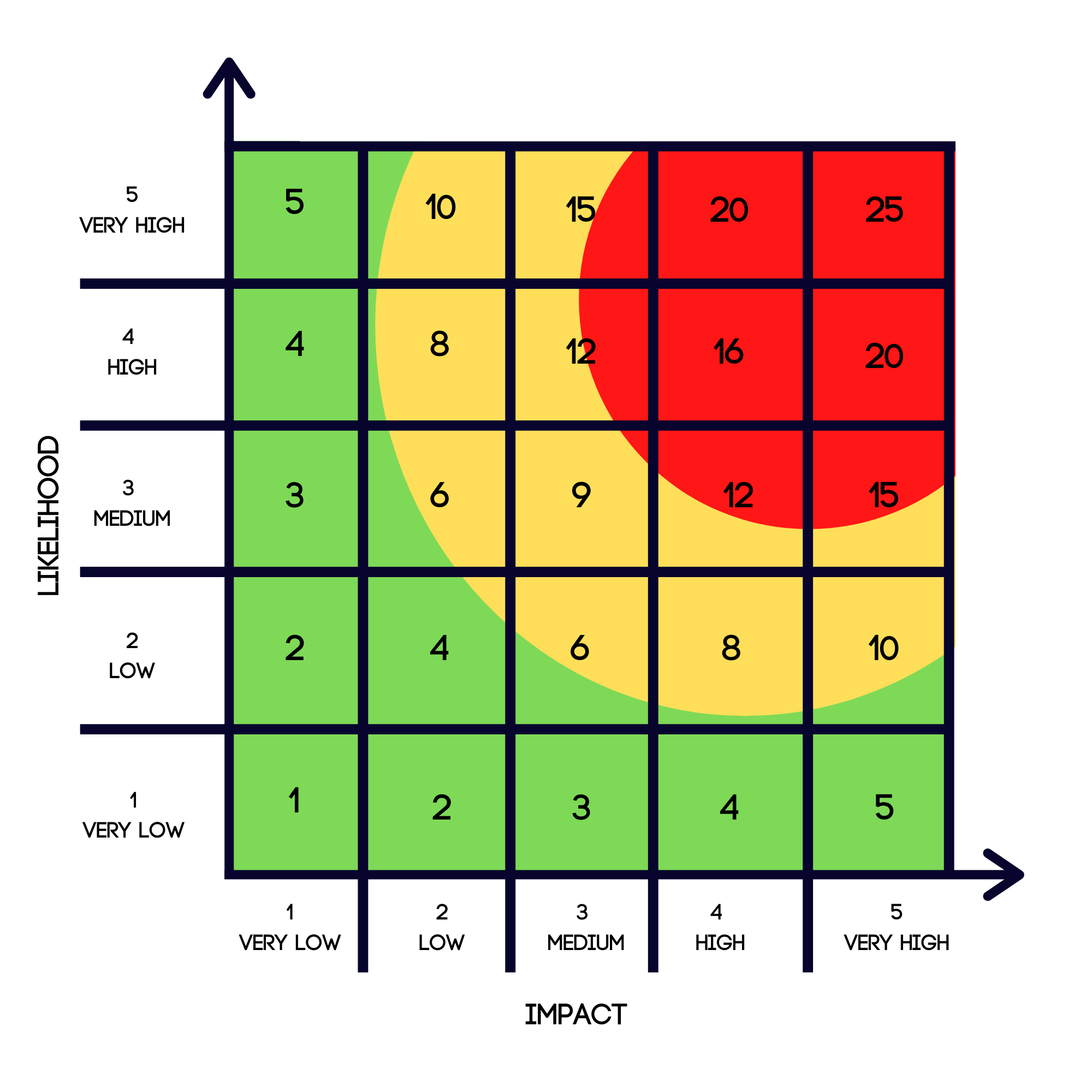
Those gaps that you identified need to be analysed to understand the risk that exists to the business, the likelihood of them being exploited and the impact exploitation would have. Impact multiplied by likelihood will give you the risk score as can be seen on this risk matrix. Your organisation should have decided their risk appetite level which will allow you to understand whether the risks you have identified sit out with the company’s tolerance.
Action
After you have identified and analysed your risks, it’s time to make informed choices on how best to spend your time and budget. You want to tackle your high rating risks and burn down the rest over the next 6-12 months. This will help you focus your attention and budget on the areas that need it most, making your security function lean and efficient.
Did you find security tools that did not appear to mitigate any threats? If so, seriously consider whether you need them or not. You may have bought tools but not managed to fully utilise them or bought them because they seemed like they would mitigate a risk you thought you had. If you are stuck in a contract, put the tool to work and ask your third party how their tool can help you mitigate your high rating risks.
Measure
It is important to keep your finger on the pulse. Your risk register should be a living, breathing document that is always in a state of flux. If your risk register is stagnant then your business will be operating with an unquantifiable level of cyber security risk which is not good. Measure regularly the impact your actions are having, and you should see your overall risk position reducing. Taking this approach will allow you to provide evidence-based security recommendations across the business and if you need additional budget, you’ll have quantifiable evidence to present to management.
Recap
Risk management is your friend and should be used to guide security decisions, investments and resources day to day. It can help you stay one step ahead of threats and make proactive security decisions. If you would like help embedding risk management into your security function then get in touch with Neon Circle.



